フリーソフト の概要
スマートフォンが普及してモバイルアプリで広告や個人情報の収集による収益化が図れるようになったため、Windowsで動作する現行のフリーソフトは オープンソース で開発されているものと、有料アプリの基本機能を利用できるフリーミアムアプリが多く、セキュリティソフトがアドウェアを PUP/ SUS としてブロックするようになったこともあり、一昔前に比べるとアドウェア や スパイウェア などのリスクは低減している。
オープンソースソフトウェア
オープンソースソフトウェア はプログラムの設計図であるソースコードを公開しているもので、アプリが実行するプロセスを確認できるため、アプリの安全性がソースコードのレベルで 担保されている。
OS のアーキテクチャ
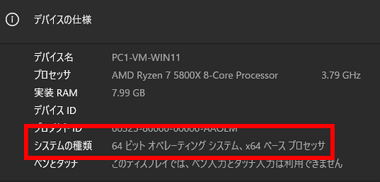
32bitは 2の 32乗(約42億)、64bitは 2の 64乗(約 1844京 6744兆 737億 )の情報量を 1度に処理でき、32bitに比べ 64bitは格段に処理能力が高くなる。
32bit の Windowsは RAMを最大 4GB、ハードディスクは最大 2TBしか認識しないが、64bit は Windows 10 Home で RAMを 128GB、Proだと 2TBまでサポートしており、HDDは GPT だと最大で 18EB ( エクサバイト ) まで利用できる。
ステーブル(安定)版とベータ版
- 安定版
不具合が修正されたバージョンで、通常は安定版がリリースされる、 - β版
正式リリース前の試用版で、隠れたバグの発見などを目的として提供される。 - α版
開発初期に機能など確認する開発者向けのテスト版。
インストーラーの検査
- オンラインインストーラー
インストール実行時に必要なプログラムをダウンロードするタイプで、実行するとスタートメニューへの登録やデスクトップのショートカット作成など、アプリの使用環境を整える。 - オフラインインストーラー
セットアップに必要なファイルをすべて格納したタイプで、保存しておくとアプリのバックアップになる。 - Zipファイル
アプリ本体やインストーラーの配布に使用され、 アーカイバ で 解凍してから使用する。
一昔前までは Zipファイルで配布されているプログラムはマルウェアに感染していることが多かったため、セキュリティ面からシステムドライブ(Cドライブ)に保存するのではなく、パーティションで区切った別ドライブや、増設したドライブに専用のフォルダを作成して保存することが推奨されていたが、アプリは安全性を確認してから起動するのが鉄則で、安全を確認したアプリは Cドライブ保存しても問題はない。
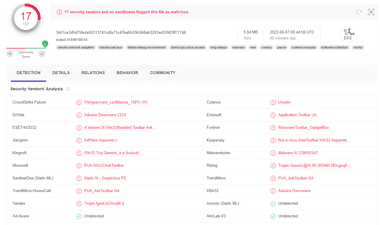
アドウェアやスパイウェアを組み込んだフリーソフトは少なくなっているが、改ざんなどの可能性もあるため、ダウンロードした インストーラーや Zipファイルは VirusTotal での検査を推奨。
- VirusTotalについては VirusTotal の概要と使い方 を参照。
VirusTotal は インストーラーやZip ファイル のリスクを確認できるが、インストール実行時にプログラムをダウンロードする オンラインタイプは 脅威を検出できない。
Windows Defender
Windows Defender は Windows 10(1703)がリリースされた 2017 年頃から脅威の検出率 が向上し、 AVAST・ESET・Kaspersky・Norton などのメジャーなサードパーティ製セキュリティソフトと比肩するレベルになり、PUP/ SUSの検出や未知の脅威を検出するヒューリスティック技術も実装しているが、インストーラーに含まれているアドウェアやブラウザハイジャッカーなどをスルーすることが多いため、フリーソフトの使用が多い場合は信頼できるサードパーティ製のセキュリティアプリの利用を推奨。
チェックサムよるデータの整合性
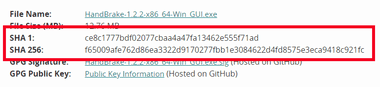
サーバにアップロードされているファイルは改ざんのリスクがあり、公式サイトから入手しても 100% 安全ではないため、サイトによっては チェックサム を表示していることがある。
チェックサム は MD5・SHA1・SHA256・SHA512 などの ハッシュ値で表示され、ダウンロードしたインストーラーのハッシュ値と照合することで インストーラーに問題がないか確認できる。
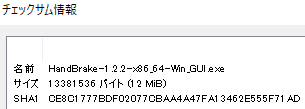
ハッシュ値は 7- ZIP や Folder Size Explorer などで確認でき、ハッシュ値が違っているとファイルのウイルス感染や改ざんの可能性がある。
ユーザーアカウント制御(UAC)
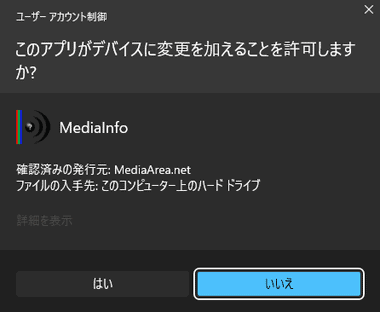
Windowsはシステムの安定性に影響を与える操作を行うと、セキュリティ対策としてユーザーに許可を求める 昇格プロンプト が表示され、デジタル署名 の情報を確認できる。
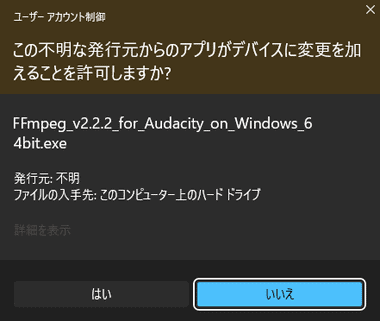
デジタル署名のないプログラムはリスクが高く、信頼できるプログラムのみ実行を許可 する。
Adw Cleaneの実行
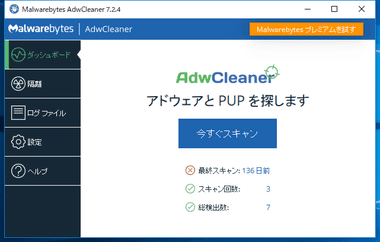
Adw Cleaner はアドウェア・スパイウェア・PUP/ PUA などの駆除に特化したフリーソフトで、アプリのインストール時やアップデート後に実行を推奨。
- Adw Cleanerについては Malwarebytes AdwCleaner のインストールと使い方 を参照。
システムのバックアップ
アプリをインストールすると、使用環境や利用方法によってはシステムに影響を及ぼし、Windows が不安定になる可能性があるため、アプリのインストール前には システムの復元 や システムイメージのバックアップ を実行し、正常な環境へロールバックできるようにしておく。
- バックアップについては Windows の バックアップ設定と復元方法 を参照。
危険なアプリ

フリーソフトやフリーミアムソフトには、ユーザーの不安を煽って有料版を購入させる 偽装セキュリティツール(ローグウェア) や、入手困難なプログラムなどに偽装している トロイの木馬 など悪質なアプリが存在する。
ワンクリック詐欺や架空請求詐欺と同じく、食指が動きやすいコンテンツや違法なプログラムはリスクが高く、ローグウェアは信用を得るために広告で露出を増やし、ユーザー評価なども捏造している。
- マルウェアについては マルウェアの種類と概要 を参照。
ユーザーエクスペリエンス向上プログラム – 匿名のデータ収集
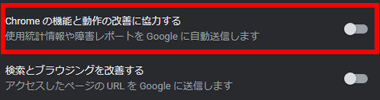
有料・無料を問わず 大半のソフトウェアには ユーザーエクスペリエンス向上プログラム として、匿名の使用データ収集が有効になっており、プライバシーポリシー に収集されたデータの用途が記載されている。
ユーザーエクスペリエンス向上プログラムでは直接個人を特定できるデータは収集されないが、ユーザーが使用しているデバイスの固有識別番号が含まれていることが多く、匿名の使用データを買い取って集約する企業は、固有識別番号からオンラインストアの利用履歴・SNSの利用履歴・動画サイトの利用履歴などを紐づけ、個人を特定できるレベルのデータに仕上げて販売している。
アンインストール
インストーラーを使用してインストールしたアプリは、Windowsの プログラムと機能 を使用してアンインストールするが、アンインストールを実行してもアプリによっては 100MB以上のファイルが削除されずに残る ので、Revo Uninstaller などの アンインストール支援アプリ を使用する。
有料版へのアップグレード
現在は購入時に更新期間を選択する サブスクリプションタイプ が主流で、買い切りタイプは「ライフタイム」や「無期限」 と表示されている。
- サブスクリプションタイプ
常に最新のアプリを使用でき、サポートも受けられるが、サブスクリプションが自動更新に設定されていることが多く、定期的に請求が発生する。 - 買い切りタイプ
支払いは購入時のみで、購入したアプリは無期限で利用できるが、バージョンアップは マイナーバージョンアップ(Ver 3.4 → 3.5)のみで、メジャーバージョンアップ(Ver 3.5 → 4.0)はできず、サポートも購入後 1 年間に設定されていることが多い。
サブスクリプションのキャンセル方法には管理画面から設定できるものや、サポートセンターへ連絡が必要なものなどアプリによって異なり、請求は決済代行会社が行っているので、アカウントを削除しても請求は止まらない。
関連記事
クリック率の低い Google AdSense のバナーを 置き換えるだけでも 収益の改善が期待できる 1000回の広告表示 ( CPM ) で収益が発生する広告配信プラットフォーム
パソコンのハードウェア情報に紐付けられている DVDFabや StreamFabの ライセンスを別のパソコンに移行する方法と、ライセンスの強制解除、ライセンスの再認証の方法など DVDFabのライセンス認証解除と再認証の手順
DVD/ BDのコピーガード解除機能を実装した コピー・リッピングソフトや動画エンコーダー、DRM解除アプリ、動画ダウンローダーなどをリーズナブルプライスでリリースしている Leawo のセール情報と購入手順・ライセンス登録方法
ロゴなどの画像から類似フォントの検索・ダウンロードができる Font Finder Tools サイトの紹介と、What Font is.comなど各サイトの使い方
暗号化されたストレージにデータを保存するアプリと、エンドツーエンドで暗号化されるゼロナレッジのメモアプリの違いや、ゼロナレッジでプライバシーを重視した代表的なメモアプリを紹介。


