マルウェアとは
Malware(マルウェア)は Malicious softwere(悪意のあるソフトウェア)の 混成語で、ウイルス・ワーム・トロイの木馬・スパイウェア など 悪意のあるコードを含んだ プログラムの 総称。
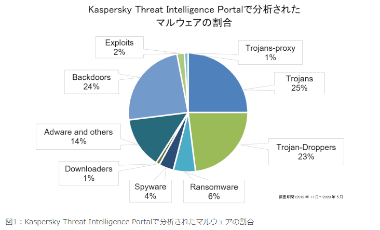
近年は トロイの木馬 による攻撃が増加 している。
ファイルレス 攻撃
ファイルレス攻撃 はマルウェアのような実行ファイルがなく、Windows標準のスクリプト言語 Powershellなどを利用して攻撃するもので、企業などをターゲットにする 標的型攻撃 で増加している。
マルウェアの感染経路
オンラインのパソコンは常に脅威に晒されている状態だが、マルウェア感染はユーザーの過失に因るところが大きい。
- メールの添付ファイル
最も一般的なマルウェアの感染経路はメールの添付ファイルで、不審なメールを開くだけで感染することもある。 - ウェブサイトのリンク
ワームやウイルスが仕組まれたウェブページを開いたり、リンクをクリックすることで感染する。
怪しいページに近づかなくても一般企業の公式サイトや官公庁のサイトがクラッキングを受けて改竄され、サイトへアクセスするとマルウェアが仕組まれているページヘ転送されるケースもある。 - フリーソフトなどのインストールによる感染
多くはトロイの木馬の偽装として魅力的な機能を持つフリーソフトとして公開されているが、インストールすると悪意のあるコードが実行される仕組みになっている。 - USBメモリなどメディアからの感染
Windowsの初期設定で有効になっているドライブの自動読込みを利用し、マルウェアに感染した PCに USBメモリを接続することでメディアが感染し、感染した USBメモリを別の PCに接続することで感染が広がるもので、オフラインでも拡散していくのが特徴。 - ネットワーク接続による感染
ワームの中には IPアドレスを自動生成して手当たりしだいに攻撃する無差別テロのようなタイプが存在し、インターネットに接続しているだけで感染する可能性がある。
代表的なマルウェアの形態
マルウェア には大きく分けて 4 つの形態があり、単体で動作する 従来型 から 攻撃者 が用意したサーバから プログラムをダウンロードする ダウンローダ によって PC 内に様々な 悪意のあるプログラムを設置する 多段型の シーケンシャルマルウェア が増加している。
- コンピュータウイルス
生物に感染するウイルスのように単体では増殖することができず、他の細胞(プログラム)に寄生(改ざん)して活動する。 - ワーム
他のプログラムを必要とせず、単体で活動して自己増殖する。 - トロイの木馬
フリーソフトなどに偽装してインストールを促し、プログラムが インストールされたパソコンは攻撃者からコントロール可能になる。 - スパイウェア
コンピューター内部の情報を外部へ送信するプログラム。
コンピュータウイルス
狭義での コンピュータウイルス は自己増殖できないプログラムで、近年は減少傾向にある。
- マクロウイルス
Microsoft Officeの Wordや Excelに実装されている「マクロ」を悪用したウイルス型に属するマルウェア。
Word・Excelを開いてマクロ を有効すると悪意のあるコードが実行される原始的なマルウェアで、メールの添付ファイルとして送付される。 - ドキュメントファイル ウイルス
マクロウイルスと異なり マクロ機能ではなく Word / Excel / Power Point のほか、PDFなどのドキュメントファイルに仕組まれているウイルスで、ファイルを開いたりドキュメント内の画像をクリック、PowerPoint のスライドショー実行などで感染する。
トロイの木馬
トロイの木馬 はアプリなどに偽装してコンピュータに侵入するタイプのマルウェアで、感染するとコンピュータの制御やセキュリティシステム全体を乗っ取ることも可能な脅威。
ユーザーが自身がウェブサイトや SNS/ メールの URLなどから 偽装したトロイの木馬のダウンロード・実行 することで感染する。
- バックドア
通常の認証経路をバイパスしてコンピュータに侵入する仕組みで、トロイの木馬としてインストールされるほか、ファームウェアなどに意図的に組み込まれる場合があり、バックドアがインストールされると攻撃者は不正アクセスやマルウェアの転送作業が行えるようになる。 - トロージャンドロッパー
トロイの木馬としてユーティリティソフトなどに偽装して パソコンに侵入し、ドロッパー内部の不正プログラムを実行するか、ダウンロードプロセスを自動実行してマルウェアをダウンロードする。
ドロッパー自体には不正コードが含まれていないか、不正コードを暗号化するなどしてセキュリティソフトの検出を回避する特徴がある。 - トロージャン ダウンローダー
ドロッパー で ダウンロードプロセスを実行するタイプの別称。
トロイの木馬 としてパソコンに侵入してマルウェアをダウンロードする脅威で、近年 増加している「シーケンシャルマルウェア」で利用される。 - キーロガー
キーボードで行ったすべてのキーストロークを記録するもので、キーロガー 自体はトロイの木馬ではないが、ユーザーのログイン情報などを盗む手段として、トロイの木馬に組み込まれることが多い機能。
スケアウェア
スケアウェア はユーザーの不安を煽るマルウェアの総称で、トロイの木馬やウイルス として感染する。
- ランサムウェア
感染したパソコンを完全にロック状態にし、パソコンに保存されたデータの復元を条件に身代金を要求してくる。 - ローグウェア(偽装セキュリティツール)
閲覧中のウェブサイトがウイルス感染しているようなポップアップ表示などで偽装したセキュリティアプリのインストールを促し、アプリをインストールすると偽のウイルス駆除のために有料版の購入が必要になり、個人情報やクレジットカード情報が盗まれる。
アドウェア
アドウェアは 広告を表示させるプログラムで、他の脅威に比べ実害は少ないが、ポルノを含めた大量の広告を表示させるなど迷惑なものもあり、スパイウェアの性質を備えている脅威も存在する。
- ブラウザハイジャッカー
ブラウザハイジャッカー は ブラウザの設定を変更して 元に戻せなくなる 迷惑なプログラムで、ホームページの変更 , 検索エンジンの変更 , ツールバーの変更 , 広告のポップアップ表示 などが行われる。
従来ブラウザハイジャッカーはフリーソフトのインストーラーにバンドルされていたが、現在はブラウザの拡張機能(アドオン / プラグイン)として提供され、トロイの木馬と同じくユーザー自身がインストールしているケースが多い。
フィッシング
フィッシング(phishing)はログイン情報やクレジットカード情報などを盗む詐欺行為で 、通販サイトや金融会社を模倣して設計されたウェブサイトに誘導し、偽のフォームに入力させるタイプが一般的。
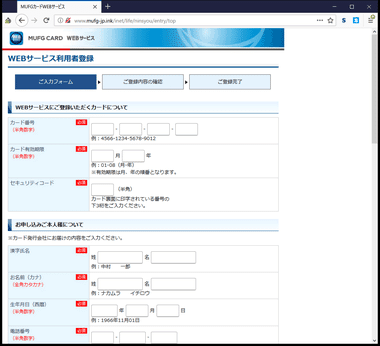
近年のフィッシングサイトはトラフィックが暗号化されていない http を使用しているなどの違いはあるものの、デザインだけ見ると本物と見分けがつかないほど精緻に作り込まれているものが増加している。
- ファーミング
DNSの設定や HOSTファイルを書き換えて偽のサイトに誘導するもので 、ブックマークや検索結果に表示されているリンクからでも偽のサイトにリダイレクトされるため、ユーザーが気づきにくく被害に遭いやすい。 - スパム
無差別に一括して大量にメールや SNSなどにメッセージを送信する迷惑行為で、主に広告や宣伝に利用されるが、中にはフィッシングサイトへ誘導する なりすまし もある。
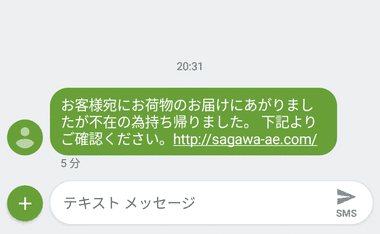
SNS に送信される不在連絡の「なりすまし」は被害が多いため、リンクをクリックする前に URLの確認は必須。
ルートキット
ルートキットは攻撃者が攻撃対象のコンピュータをリモート操作するのに必要なマルウェア一式で、トロイの木馬などでコンピュータに侵入すると自らを隠蔽してセキュリティアプリからの検出を回避し、キーロガーやバックドアの設置、システムの改ざん、機密情報の抜き取り、有害コードの隠蔽などが行われ、感染していることに気付きにくいため被害が拡大する傾向にある。
クライムウェア
クライムウェア は犯罪行為を目的 をしたマルウェア の総称。
エクスプロイト
エクスプロイトは OS やソフトウェアの脆弱性(セキュリティホール)を悪用して攻撃を行うマルウェアで、未知の脆弱性を利用するゼロデイ攻撃は被害が甚大になりやすい。
ボットネット
ボット は感染したコンピュータをネットワーク経由で 外部から遠隔操作 できるようにするマルウェアで、トロイの木馬やメールの添付ファイル、改ざんされたウェブサイトへのアクセスなどで感染する。
ボットネット はボットをネットワーク化したもので、ボットを制御する C&C(Command and Control )サーバー などのボットマスター からゾンビ化した多数のコンピュータに指令を出し、DDoS のような大規模な攻撃に利用する。
DDoS
多数のコンピュータから 1つサーバーへ膨大なトラフィックを送信し、サーバのリソースを消費してシステムをダウンさせたり、セキュリティ機能を無効にしてデータを盗むことができるようにするもので、企業や官公庁などがターゲットにされやすい。
感染の予防
マルウェア感染の予防策は、不審なファイルやメールを開かない・怪しいサイトやリンクは踏まない・信頼度の低いアプリはインストールしない など、 ユーザーの慎重な行動と Windowsやアプリケーションを最新の状態にすることが最も効果的。
- ルーターの導入
無線 / 有線を問わず インターネット接続の 際にパケットフィルタリングなどのセキュリティ機能が備わっているルーターを使用することで、不正アクセスに対してのセキュリティが向上する。 - セキュリティアプリの導入
有料のセキュリティアプリには Microsoft Defenderにはないブラウジングの保護や、ゼロデイ攻撃など未知の脅威への対応、 ネットワークの保護など多様化するセキュリティリスクに対応しており、Microsoft Defenderよりも強力な保護を期待できる。
感染が疑わしい場合の対処法
パソコンの起動や処理が突然遅くなった場合や、直近の操作でマルウェアの感染が疑われる場合、パソコンの操作可能であれば Windowsをアップデートし、セキュリティソフトを使用している場合は ウイルス定義を最新の状態にしてから、以下の順序でセキュリティアプリを実行する。
- Microsoft Defenderの オフライン スキャンを実行
- 起動ディスクからスキャンする Kaspersky Rescue Disk を実行
関連記事
エンタープライズ(企業向け)レベルの高度なセキュリティ環境を実現し、ディープ・ラーニングによってゼロディ攻撃にも対応、複数デバイスの一元管理も可能な信頼度の高いセキュリティアプリ
マルウェアの検出・リアルタイム保護・危険サイトのブロックをエンタープライズレベルで利用でき、ディープ・ラーニングによってゼロディ攻撃にも対応している信頼度の高いセキュリティアプリ
リアルタイム保護などの基本的なウイルス対策機能のほか、プライバシー設定・アプリ/ ドライバのアップデーターも利用できる 無料セキュリティソフト
Index Kaspersky Free の特徴開発元ダウンロードシステム要件保護される主な項目インストールKaspersky Free の使い方 Kaspersky Free の特徴 マルウェアから…
Index Panda Dome free antivirus の特徴開発元ダウンロードシステム要件インストールPanda ニュースの非表示設定Panda Dome free antivirus の使…


