VPNサービスを利用するメリット
- トンネリングによる通信の保護(盗聴の防止)
- 暗号化による通信の秘匿化(盗聴の防止・プライバシー保護)
- 専用 DNSの利用による通信の匿名化(プライバシー保護)
- 接続先のロケーション変更による位置情報の偽装(ジオブロックの回避)
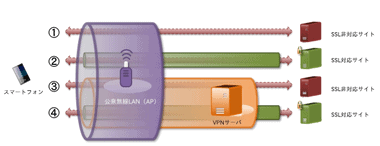
VPN(仮想プライベートネットワーク)は、 通信する際にトンネルを作って外部から遮断された仮想回線で二点間を直結(トンネリング)し、トンネルの中の通信を暗号化して内容を保護するだけでなく、VPNサーバを経由するので接続元の IPアドレスが匿名化され、プライバシーの保護が確保される。
フリースポットのリスク
通信のセキュリティは Googleがウェブブラウザとサーバ間の通信を暗号化する HTTPS を推進したことで、HTTPSのトラフィックは 2017年に 90%を超え、 HTTP接続で問題だった 中間者攻撃(Man-in-the-middle attack)による盗聴リスクは大きく減少したが、スマホの普及で増加した Wi-Fiのフリースポットが Wi-Fiハッカーによる 盗聴 や なりすまし のリスクに晒されている。
IPAテクニカルウォッチ「公衆無線LAN利用に係る脅威と対策」
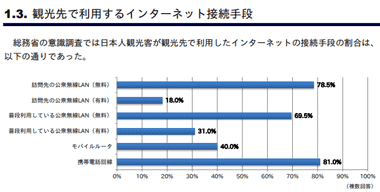
日本人観光客の 4 人のうち 3 人は訪問先のフリーWiFi を利用しているが、フリー スポットを利用する機会が多いスマートフォン用のアプリは通信が暗号化されていないものが多く、通信内容を保護するために IPA(情報処理推進機構)は VPNサービスの利用を推奨している。
ISPによるログの保管と検閲
インターネットへは ISP(インターネット・サービス・プロバイダー)を通じて接続するが、ISPはネットワークを通過した通信に対してログを取っており、裁判所の令状など法的根拠に基づいた個人情報開示請求が承認されると、サーバにアクセスした IPアドレスから契約者の氏名・住所などが割り出されて開示される。
通信の秘密
日本にはプライバシーを保護する 電気通信事業法 第 4 条 第 1 項 通信の秘密 で、通信の内容や宛先を第三者に知られたり、漏洩されたりしない権利が保障されており、本人の同意を得るか、正当行為・正当防衛・緊急避難に該当する「違法阻却事由」がある場合にのみ通信の秘密の侵害が許される。
2018年 4月 政府は ISPに漫画村・Anitube・Miomioの 3 サイトをブロッキングするよう要請したほか、警察庁などによって児童ポルノ関連のサイトの閲覧制限も実施されている。
シギント(通信の傍受)
エドワード・スノーデン氏が NSA(アメリカ国家安全保障局)による国際的監視網(PRISM)の実在を暴露したことで、都市伝説的だった公的機関による シギント(通信の傍受)への警戒感が強くなり、個人レベルでもプライバシーの保護対策を講じる人が増加している。
米英など5カ国「ファイブアイズ」、日独仏と連携 サイバー攻撃、中国の機密情報共有
VPN接続による通信の匿名化
ジオブロックの回避
VPNプロバイダは世界各国にサーバを設置しているため、海外からの接続を受け付けていないサイトへは対象国 の VPNサーバに接続することで位置情報を偽装してアクセスが可能になる。
プライバシー保護のための VPNプロバイダの指標
VPNは通信の安全性とプライバシー保護に有用なサービスだが、VPNプロバイダは ISPにようにユーザーのトラフィック情報を収集可能で、プライバシー保護には VPNプロバイダの信頼性が重要になる。
- 独立した第三者機関の監査
サーバーセキュリティ会社などの第三者機関からデータの取扱などの監査を受け、レポートを公開していると、最も確実な安全性の担保になる。 - ノーログ
アクセスログを保存しないノーログポリシーは VPNプロバイダーの自己申告で、過去にはノーログポリシーを採用していながらログデータを提供した事案も発生しているため信憑性は高くないが、プライバシー保護には必須の条件。 - DNSリーク(DNS漏れ)
VPNサービスでは暗号化された DNSサーバを利用するので、アクセス元の IPアドレスは見えないのだが、見えないはずの IPアドレスが見えてしまっている状態が DNSリーク(DNS漏れ)。
暗号化された DNSサーバへの接続が切断されると、DNSクエリは暗号化されていない ISPの DNSサーバなどに転送されて通信を維持するため、VPNサービスは強制的にネットワークを遮断するキルスイッチなどを実装して DNSリークを阻止している。 - プロバイダの拠点
ノーログポリシーを採用しているプロバイダでも公的機関から法的に特定 IPアドレスの監視や、アカウントのロギングを強制される可能性があり、 イギリス領ヴァージン諸島 ・パナマ・セイシェル・ケイマン諸島・マレーシアは「プライバシーヘイブン」と呼ばれる法的にユーザーのプライバシーが保護される国で、トップVPNプロバイダが拠点を置いていることが多い。 - 令状のカナリア(透明性レポート)
VPNプロバイダなど個人情報を取り扱う企業が公的機関からデータ提出要求を受けていないことを表しているが、令状のカナリアに法的根拠はなく、 安全性を保証したものでもない。
VPNプロバイダにはノーログポリシーを採用していないところも多く、特に無料で提供されているモバイル用の VPNアプリでは、ユーザーのアクティビティを広告やトラフィックの分析データとして利用したり、プライバシーポリシーに収集したデータの利用方法が記載されていないなど、信頼に値しないサービスが多い。
DNSリークのテストツール
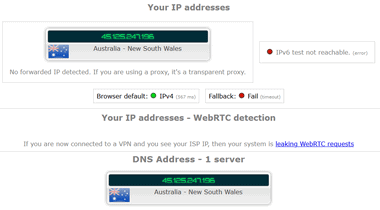
VPN接続が確立している状態で ipleak.net へアクセスし、Your IP address に接続先のサーバ情報のみが表示されるか、接続先サーバと DNSサーバに同じ国が表示されていれば DNS漏れはなく、通信は匿名化されている。
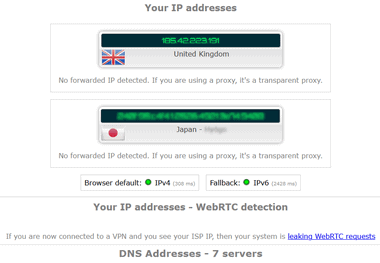
DNS漏れが発生していると DNSサーバが国内になるなど接続先のサーバと違っている。
VPNプロバイダのサイトにある IPアドレスチェッカー・DNSリークテスト・WebRTCリークテスト などを使用すると「漏洩している」と表示されるが、VPNプロバイダのツールは自社の VPNサービス以外の環境からのアクセスはすべて漏洩と表示されるので、まったく信用に値しない。
通信速度のテスト
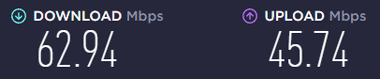
SPEEDTEST で VPN接続時と未接続時で測定し、大きな速度低下がないことを確認する。
プロバイダの統合
近年 VPNプロバイダは買収によって統合が進んでいる。
Nord Security
リトアニアの Nord Security は NordVPN を提供している VPNトッププロバイダ。
Kape Technologies
Kape Technologies PLC はイスラエルの富豪 Teddy Sagi氏が所有するサイバーセキュリティ会社。
- 2017年3月:CyberGhost を買収
- 2018年10月:ZenmateVPN を買収
- 2019年 11月:Private Internet Access を買収
- 2021年 9月:ExpressVPN を買収
Kape Technologies の前身はブラウザ拡張機能を開発した Crossrider で、開発したプログラムがマルウェアに利用されたことから悪名を轟かせ、Teddy Sagi 氏も過去に賄賂と詐欺の罪で有罪になったこともあり、買収された VPNサービスの安全性が危ぶまれているが、 Crossrider は 2016年に経営陣を一新してプログラム開発会社からサイバーセキュリティ会社に転向しており、買収された VPNプロバイダも独立運営している。
VPNの信頼を損なう事案
PureVPN によるネットワークログの提供問題
ノーログポリシーを採用していた PureVPNは、2017年に FBIの要請に応じてネットワークログ(ユーザーが PureVPN に接続した記録)を提出してユーザーの特定に協力。
PureVPNは提出したネットワークログはトラブルシューティングなどで使用するために自動生成されるもので、ユーザーのアクティビティは保存されていないと釈明したが ノーログポリシー の信頼性が大きく損なわれることになった。
2018年に PureVPNはプライバシーポリシーを改定し、米国の情報システム監査人 Altius IT よりゼロログ認定を受けており、現在はユーザーのアクティブログから個人を特定することができない。
Hotspot Shield Free VPNによる広告ネットワークへのルーティング問題
米国に本拠を置く非営利団体 Center for Democracy & Technology は、2017年に Hotspot Shield Free VPNがユーザートラフィックを広告ネットワークへルーティングしていることを指摘。
当時の Hotspot Shield Free VPN のプライバシーポリシーはユーザートラフィックが保存され、第三者に開示できるという内容になっていた。
Hotspot Shield Free VPN は 2018年 6月にプライバシーポリシーを改定し、ユーザートラフィックは保存せず、Hotspot Shield Free VPNのみユーザーの位置情報が広告に使用されるなど表記が具体的になり、以前よりもプライバシー保護が強化された内容になった。
Onavo Protect による ユーザーデータ収集の問題
Facebookに買収されたイスラエルのソフトウェアベンダー Onavoは、提供していた 無料 VPN アプリ Onavo Protectを使用して送信されてきたトラフィックを分析し、Facebookが買収などの営業戦略に利用していたことが明るみに出て大きな問題になり、VPNアプリがスパイウェア として機能することを知らしめる事になった。
Onavo Protect は Google Playストア から 削除されている。
Hola VPNによる出口ノード利用とトラフィック販売問題
イスラエル の ソフトウェアベンダー Hola が提供していた Hola VPN では、 ユーザー のデバイスを出口ノード(最終的にサーバへアクセスする IP)として使用していることが発覚し、VPNユーザーの帯域幅が 1GB あたり 20ドルで販売されていた。
出口ノードとして犯罪に利用されると パソコン遠隔操作事件 のように全く覚えのない犯行の容疑者として検挙される可能性がある。
関連記事
プライバシー保護のためノーログポリシーを採用し、キルスイッチやスプリットトンネリング、P2P接続、悪質な広告やマルウェアなどのブロックもサポートしている セキュアな VPNサービス
プライバシー保護のためノーログポリシーを採用し、キルスイッチやスプリットトンネリングもサポートしている 月間 10GBまでデータ転送が可能な セキュアな無料 VPNサービス
日本・米国・英国・オーストラリア・ドイツ・フランス に無料サーバがあり、1 日 700MB まで無料利用できるが 実態が不透明な 中国の VPN サービス
Index Proton VPN の特徴開発元ダウンロード仕様安全性システム要件Protonアカウントの取得(購入方法)インストール設定ProtonVPN for Windows の使い方DNS漏れの…
Index Proton VPN Free の特徴開発元ダウンロード仕様安全性システム要件Proton アカウントの作成インストール設定Proton VPN Free の使い方DNS漏れの確認パスワー…

